Why AI-Driven Logistics and Supply Chains Need Resilient, Always-On Networks
Modern supply chains are extremely complex, intricate, and expansive, comprising many parties (like brokers, shippers, and warehouses) that must communicate and operate in a timely and organized manner. Like any ecosystem, one small disruption can affect the larger environment in […]
The post Why AI-Driven Logistics and Supply Chains Need Resilient, Always-On Networks appeared first on TechSpective.
Humanoid robot achieves controlled flight using jet engines and AI-powered systems
Seeing through a new LENS allows brain-like navigation in robots
Hexagon launches AEON, a humanoid built for industry
Why your agentic AI will fail without an AI gateway
Agentic AI is powerful. But without control, it can quickly become a chaotic liability.
As AI systems evolve into more dynamic, generative, and agentic approaches, complexity, cost, and governance challenges multiply.
That’s where an AI gateway comes in.
Think of it like a smart home hub: centrally coordinating devices, enforcing rules, and keeping everything running smoothly.
An AI gateway plays the same role for agentic AI workflows routing tasks, enforcing policies, and reducing infrastructure friction — all in a simple, low-effort way that doesn’t overload your team.
What is an AI gateway?
An AI gateway is a lightweight, centralized layer that sits between your agentic AI applications and the ecosystem of tools, APIs, and infrastructure they rely on.
What it’s not
An AI gateway is not a model, an app, or just another tool in the tech stack. It’s a unifying interface that brings control, abstraction, and agility to your entire AI ecosystem.
What it unlocks
- Routing and orchestration improve as tasks are automatically directed to the right tools or services based on cost, performance, or policy. Instead of hardwiring logic into every agentic workflow, IT and governance teams stay agile and in control.
- Policy enforcement becomes scalable by applying governance and compliance rules across a web of tools, environments, and teams. What’s usually difficult to standardize in a complex agentic ecosystem becomes consistent and automatic.
- Abstraction and flexibility grows as teams evolve workflows or swap components without rearchitecting systems, adding headcount, or risking costly downtime.
- Operational confidence grows as agentic systems scale with centralized oversight and real-time visibility. Teams can move faster, knowing they’re not trading speed for cost, control, or compliance.
Why AI leaders should care
As agentic AI systems grow, so do the number of tools, models, APIs, and workflows they depend on. Without a unifying layer, every new addition increases complexity and raises the cost to maintain it.
An AI gateway keeps AI cost sprawl in check by:
- Minimizing redundancies
- Reducing tooling overhead
- Improving infrastructure efficiency.
You avoid paying twice (or three times) for capabilities that should be orchestrated, not duplicated.
It also reduces enterprise risk.
By enforcing governance policies and providing oversight across a fragmented yet complex AI stack, an AI gateway ensures consistency as you scale.
Whether you’re adding new agents, adapting to new regulations, or deploying across new environments, it helps standardize compliance, control, and reduce operational gaps.
Because it sits independently from any single model, tool, or cloud provider, an AI gateway gives you the flexibility to evolve your AI systems without getting locked in. You can swap agentic components, optimize for cost or performance, and adapt to change without starting from scratch.
Without an AI gateway, every change becomes rework, and your team ends up drowning in bespoke system maintenance while struggling to manage growing risks.
How AI gateways reduce cost, risk, and friction
Here are just a few examples of how an AI gateway streamlines complexity as your systems scale.
Swapping an LLM for a cost-efficient one
Without a gateway:
Teams have to manually rewire workflows, risking broken chains, regressions, and delays. What should be a cost-saving move ends up burning time, resources, and budget.
With a gateway:
A simple routing update handles the change. You can swap out an LLM agent or update an agentic flow without rearchitecting — so cost savings don’t come with hidden costs.
Responding to a regulation change
Without a gateway:
Every agent and its tool stack must be assessed and updated manually, creating delays and compliance gaps.
With a gateway:
You apply the policy once, and it’s enforced consistently across all tools and environments.
Adding a new tool to an agentic chain
Without a gateway:
Integrations are brittle and often lead to downtime or duplicated effort.
With a gateway:
Plug-and-play orchestration allows you to test and introduce new tools quickly while maintaining consistent governance and reliability.
What breaks without an AI gateway
The risks compound quickly. As your AI systems evolve, so do the dependencies, costs, and failure points. Without a unifying layer, every new tool, workflow, or requirement adds overhead, complexity, and risk.
Skyrocketing infrastructure costs
Redundant tools, compute inefficiencies, and custom integrations drive up operating expenses (OPEX) and capital expenses (CAPEX) at an unsustainable pace.
OPEX drivers:
- Redundant workflows repeatedly calling external APIs or LLMs
- Increased FTE hours spent on manual tracing, monitoring, or stitching together tools
- API and SaaS sprawl as siloed tools each require separate contracts and maintenance
CAPEX drivers:
- Custom infrastructure built per use case, like duplicative vector databases or tool registries
- One-off governance tooling developed app-by-app
- Underused hardware or software licenses with no shared orchestration layer to optimize usage
Security and governance blind spots
Without a centralized layer, there’s no consistent way to enforce policies, monitor usage, or trace agent behavior, making governance fragmented and incomplete.
Rigid, brittle systems
Tool swaps or workflow changes become high-effort, high-risk projects. Even small updates can require full rework, slowing innovation and adding operational drag.
Why this matters now
The age of agentic AI is arriving faster than most teams are ready for.
What started as experimentation is quickly shifting to production, moving from linear pipelines to dynamic, autonomous systems. But many organizations are layering this complexity onto brittle, point-to-point architectures that can’t keep up.
An AI gateway is not a future luxury. It is what prevents today’s agentic experiments from becoming tomorrow’s operational nightmares when autonomous workflows multiply, new regulations emerge, or tool sprawl explodes.
The longer you wait, the harder it becomes to retrofit abstraction, control, and agility into a system that was not built for agents. An AI gateway lays the foundation now so you can scale agentic AI with speed, security, and confidence later.
Common misconceptions about AI gateways
If AI gateways feel unfamiliar or confusing, you’re not alone. Let’s clear up a few of the most common misconceptions.
“Our stack already covers orchestration and governance.”
Unless you have a unified layer that orchestrates, provisions, swaps, and governs all your AI agents and integrations — without vendor lock-in — you don’t have a true AI gateway. Most tools only simulate fragments of this.
“This is only for advanced, multi-agent systems.”
Even simple single-agent systems benefit. Gateways eliminate technical debt before it multiplies.
“Isn’t this just more overhead?”
No. Gateways eliminate overhead by reducing integration work, unifying control, and minimizing compliance risk, while also helping you optimize for cost across tools, agents, and environments.
“Won’t this lock us in?”
A true gateway is vendor-agnostic. It actually protects you from deeper tool lock-in by decoupling your apps from specific APIs.
Get ahead of AI complexity with the right foundation
If agentic AI is on your roadmap, now’s the time to lay the foundation.
An AI gateway gives you the control, flexibility, and cost discipline to scale with confidence, without the architectural growing pains.
Want to scale agentic AI without spiraling cost or risk?
Download The enterprise guide to agentic AI ebook for a practical roadmap to scale securely, cost-effectively, and with full control from the start.
The post Why your agentic AI will fail without an AI gateway appeared first on DataRobot.
New system reliably controls prosthetic hand movements without relying on biological signals
Gearing up for RoboCupJunior: Interview with Ana Patrícia Magalhães
 Action from RoboCupJunior Rescue at RoboCup 2024. Photo: RoboCup/Bart van Overbeeke.
Action from RoboCupJunior Rescue at RoboCup 2024. Photo: RoboCup/Bart van Overbeeke.
The annual RoboCup event, where teams gather from across the globe to take part in competitions across a number of leagues, will this year take place in Brazil, from 15-21 July. An important part of the week is RoboCupJunior, which is designed to introduce RoboCup to school children, and sees hundreds of kids taking part in a variety of challenges across different leagues. This year, the lead organizer for RoboCupJunior is Ana Patrícia Magalhães. We caught up with her to find out how the preparations are going, what to expect at this year’s competition, and how RoboCup inspires communities.
Could you tell us about RoboCupJunior and the plans you have for the competition this year?
RoboCup will take place from 15-21 July, in Salvador, Brazil. We expect to receive people from more than 40 countries, across the Junior and Major Leagues. We are preparing everything to accommodate all the students taking part in RoboCupJunior, who will participate in the Junior Leagues of Soccer, Rescue and OnStage. They are children and teenagers, so we have organized shuttles to take them from the hotels to the convention center. We’ve also prepared a handbook with recommendations about security, places they can visit, places to eat. The idea is to provide all the necessary support for them, because they are so young. We’re also organizing a welcome party for the Juniors so that they can experience a little bit of our culture. It will hopefully be a good experience for them.
The Juniors will be located on the first level of the mezzanine at the convention center. They will be separate from the Major Leagues, who will be on the ground floor. Of course, they’ll be able to visit the Major Leagues, and talk to the students and other competitors there, but it will be nice for them to have their own space. There will also be some parents and teachers with them, so we decided to use this special, dedicated space.
 RoboCupJunior On Stage at RoboCup 2024. Photo: RoboCup/Bart van Overbeeke.
RoboCupJunior On Stage at RoboCup 2024. Photo: RoboCup/Bart van Overbeeke.
Do you have any idea of roughly how many teams will be taking part?
Yes, so we’ll have about 48 teams in the Soccer Leagues, 86 teams in the Rescue Leagues, and 27 in OnStage. That’s a lot of teams. Each team has about three or four students, and many of the parents, teachers and professors travel with them too. In total, we expect about 600 people to be associated with RoboCupJunior.
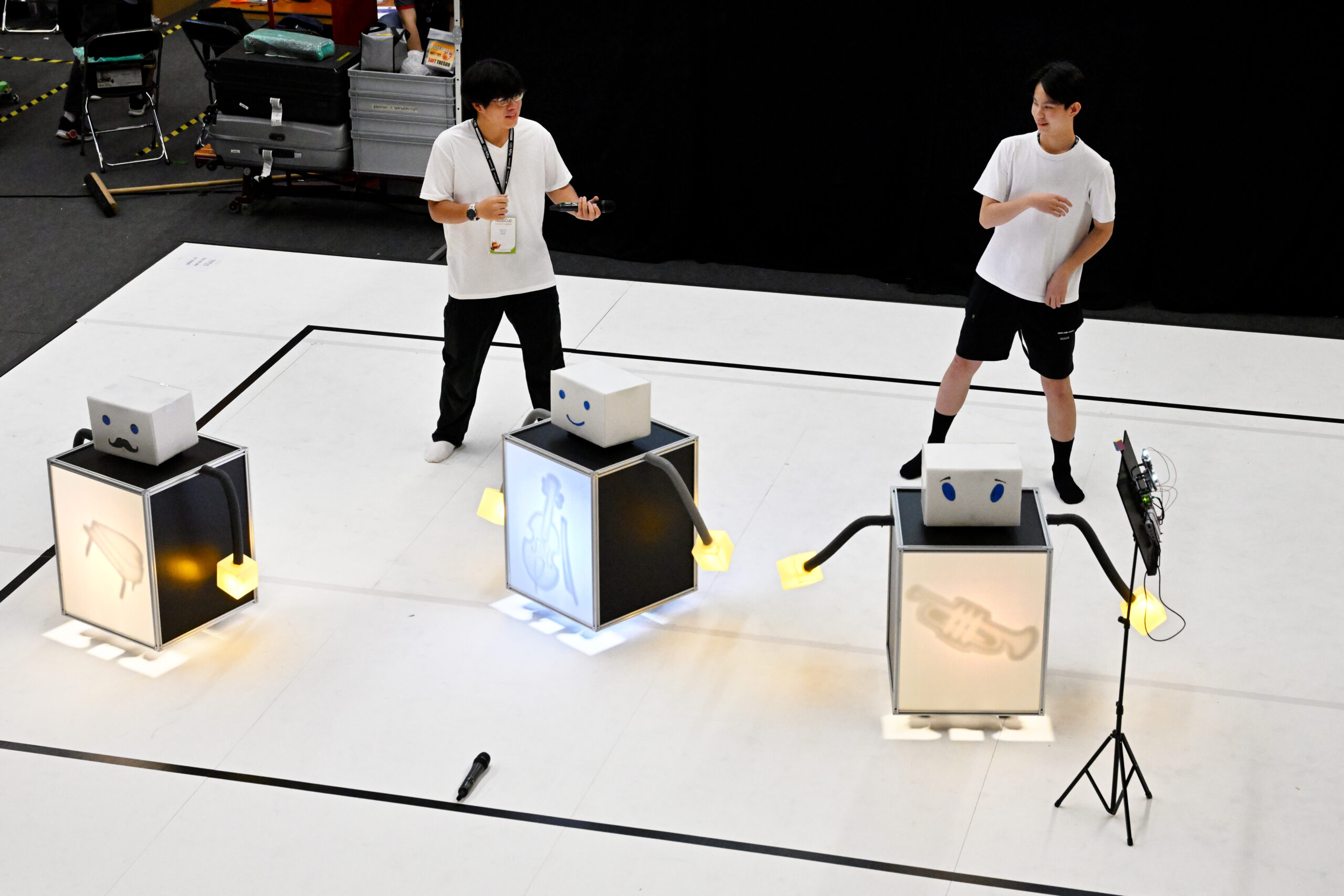
 RoboCupJunior Soccer at RoboCup 2024. Photo: RoboCup/Bart van Overbeeke.
RoboCupJunior Soccer at RoboCup 2024. Photo: RoboCup/Bart van Overbeeke.
Have you got more RoboCupJunior participants from Brazil this year due to the location?
Yes, we have many teams from Brazil competing. I don’t know the exact number, but there are definitely more Brazilian teams this year, because it’s a lot cheaper and easier for them to travel here. When we have competitions in other countries, it’s expensive for them. For example, I have a team here in Salvador that qualified for the super regional event in the US and our team couldn’t go. They had qualified, but they couldn’t go because they didn’t have money to pay for the ticket. Now, it will be possible for all the Brazilian teams qualified to participate because it’s cheaper for them to come here. So it’s a big opportunity for development and to live the RoboCup experience. It’s very important for children and teenagers to share their research, meet people from other countries, and see what they are doing, and what research path they are following. They are very grateful for the opportunity to have their work tested against others. In a competition, it is possible to compare your research with others. So it’s different from conferences where you present a paper and show your work, but it’s not possible to compare and evaluate the results with other similar work. In a competition you have this opportunity. It’s a good way to get insights and improve your research.
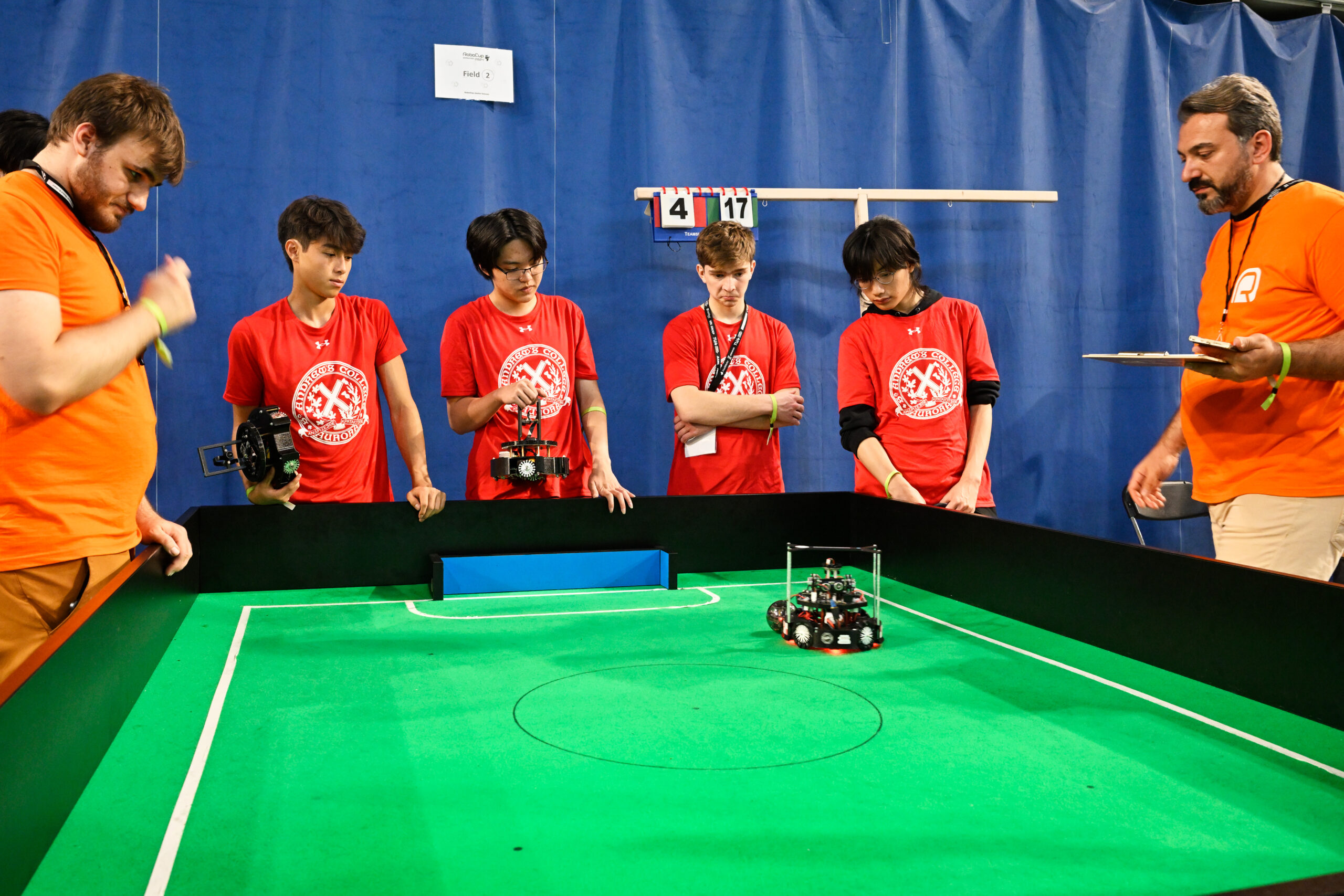
 RoboCupJunior Rescue at RoboCup 2024. Photo: RoboCup/Bart van Overbeeke.
RoboCupJunior Rescue at RoboCup 2024. Photo: RoboCup/Bart van Overbeeke.
Your role at this RoboCup will be organizing RoboCupJunior. Are you also involved in the Major Leagues?
Yes, so my main role is organizing RoboCupJunior and I am also one of the chairs of the RoboCup Symposium. Besides, some teams from my laboratory are competing in the Major leagues. My team participates in the @Home league, but I haven’t had much time to help them recently, with all the preparations for RoboCup2025. Our laboratory also has teams from the 3d Simulation Soccer League, and the Flying Robots Demo. This will be the first time we’ll see a flying robot demo league at a RoboCup.
We’ll also have two junior teams from the Rescue Simulation League. They are very excited about taking part.
 RoboCupJunior Rescue at RoboCup 2024. Photo: RoboCup/Bart van Overbeeke.
RoboCupJunior Rescue at RoboCup 2024. Photo: RoboCup/Bart van Overbeeke.
RoboCup was last held in Brazil in 2014, and I understand that there were quite a lot of new people that were inspired to join a team after that. Do you think the 2025 RoboCup will have the same effect and will inspire more people in Brazil to take part?
Yes, I hope so. The last one inspired many, many students. We could perceive the difference before and after RoboCup at that time, related to projects in schools. In 2014, RoboCup was held in João Pessoa, a city in the north east that is not as developed or populated as many other states in Brazil. It really improved the research in that place and the interest in robotics especially. After the 2014 RoboCup, we’ve had many projects submitted to the Brazilian RoboCup competition from that state every year. We believe that it was because of RoboCup being held there.
We hope that RoboCup2025 next month will have the same effect. We think it might have an even bigger impact, because there is more social media now and the news can spread a lot further. We are expecting many visitors. We will have a form where schools that want to visit can enroll on a guided visit of RoboCup. This will go live on the website next week, but we are already receiving many messages from schools asking how they can participate with their group. They are interested in the events, so we have high expectations.
We have been working on organizing RoboCup2025 for over a year, and there is still much to do. We are excited to receive everybody here, both for the competition and to see the city. We have a beautiful city on the coast, and some beautiful places to visit, so I recommend that people come and stay for some days after the competition to get to know our city.
About Ana Patrícia

|
Ana Patrícia F. Magalhães Mascarenhas received her PhD in Computer Science from the Federal University of Bahia (2016) and Master in Mechatronics from the Federal University of Bahia (2007). She is currently an adjunct professor at the State University of Bahia (UNEB) at the Information Systems course. She is a researcher and vice coordinator of the Center for Research in Computer Architecture, Intelligent Systems and Robotics (ACSO). Her current research focuses on service robotics and software engineering, especially related to the use of Artificial Intelligence (AI) in the software development process and in Model-Driven Development (DDM). |